.png)

IoT security in embedded systems: what are the challenges and solutions for deployment at scale
Why IoT security matters more than ever and how to achieve it quickly and effectively at scale.
It’s hard enough to make one internet-connected device completely safe from hackers, so how do you achieve a secure supply chain for the thousands or tens of thousands of IoT devices that could be part of a global industrial network?
Here’s the end-to-end story of chip-to-cloud security.
Contents
Part 1
Scaling securely – the main barrier to adopting IoT devices in industrial applications
The Internet of Things market isn't growing as strongly as predicted. Research firm IoT Analytics once stated by 2020 that there would be 50bn IoT devices, now there'll only be 21bn by 2025 [1][2]. Meanwhile, Gartner claims that 80% of IoT projects fail before they're even launched [3].
The limiting factor has been a compromise between security and scalability, remembering that anything connected to your network can be an entry point for hackers to take control of everything on that network.

Until now, strong security has been difficult to scale and companies have struggled to bridge the IoT scaling gap cost-effectively.
How great is the IoT security threat and what’s the industry doing about it?
Cyber attacks are increasing exponentially. Forbes reported a 300% increase in compromise of billions of IoT security devices in 2019 [4].
Cyberattacks on UK businesses jumped a fifth in 2020 [5]. Horror stories abound. As a result, IoT security regulation is being developed, which will place growing pressure on businesses to conform to prescribed standards. The EU Network and Information Security Directive (NISD) imposes heavy fines for non-compliance. Singapore has its own Cybersecurity Act (CSA) and in the US, The National Institute of Science and Technology (NIST) sets out standards for safe, legal product innovation.
The fundamental principles underlying these standards include the need for a strong root-of-trust, secure lifecycle and key management, and a zero-trust approach to supply chain management.
Effective and economical end-to-end security can only be achieved by embracing a philosophy of security-by-design, rather than by trying to bolt it on as an afterthought. In fact, when done correctly, IoT security reduces costs throughout device lifecycles, rather than adding to them.

Part 2
What’s the role of cryptography in IoT security?
When IoT devices send or receive messages to a server, either in the cloud or on-premises, two fundamental conditions must exist for the data transfer to be secure.
-
The identities of the senders and recipients of data must be established beyond doubt. As a consequence, every microcontroller or other semiconductor, such as an application-specific integrated circuit (ASIC), at the heart of each IoT device must have a unique, immutable, and unforgeable identity. This is key to effective cryptography and leads to the requirement for a root-of-trust – which we address a little later.
-
The messages must be sent in such a way that only the intended recipients can interpret them, and they must not be readable or corruptible by any device that attempts to interfere with the data in transit. This requires effective cryptography.
How cryptographic algorithms are used in the IoT
As classified by The National Institute of Standards and Technology (NIST), part of the U.S. Department of Commerce, there are three types of function generated by cryptographic algorithms: asymmetric keys, symmetric keys, and hash functions.
All three are used in a secure IoT ecosystem.
-
Asymmetric cryptography is used for identity management through generating digital signatures and certificate requests, and for implementing key exchange mechanisms. Examples of frequently used cryptographic algorithms include RSA, Elliptic Curve and Diffie-Hellman. There is also a range of new algorithms being standardized by NIST to provide effective post-quantum cryptography.
-
Symmetric cryptography is used for data transfer to and from connected endpoint devices. Symmetric keys are typically 128-bit or 256-bit, while it takes a 2048-bit asymmetric key to provide a broadly similar level of security to that of a 128-bit symmetric one. IoT deployments create a lot of data, so speed is important. Also, storing smaller keys requires less silicon area on semiconductor devices, where space is at a premium. The most common example here is AES.
-
Hash functions are used for integrity checking, ensuring that received data has not been tampered with.
IoT security depends on having a unique, immutable, and unforgeable identity for each device and being able to send data securely between devices using a combination of cryptographic functions. The starting point is to ensure that your data is reaching only the intended recipients, the foundation of which is the root-of-trust.
Part 3
What is a root-of-trust, and what is a PUF?
In IoT security terms, a root-of-trust, or RoT, comprises a device’s identity and its cryptographic keys. Its purpose is to enable service providers, whose applications may reside on cloud servers or private networks, to know which devices they are talking to when data is being exchanged, and when sending instructions or updates to endpoint devices.
The RoT provides keys for secure server communications, supports secure boot when the device starts up, and secure key storage. Server-based applications use the RoT for attestation, to be sure that they are connected to the correct device.
Without a unique RoT to minimize the risk of hacking, cybercriminals and other unwelcome actors may see what data is being exchanged within a system and may be able to steal secrets or introduce instructions or code to take control of such systems, causing them to behave differently. This can have disastrous consequences for system owners or operators. To understand how bad it could be, think about sitting in an autonomous vehicle when someone with destructive ambitions takes control of your brake and accelerator.

The silicon-based hardware root-of-trust
The unique identity of a silicon chip, for example, the microcontroller at the heart of an IoT device, is a string of digits – a random number. So are cryptographic keys.
You can create them in software, but random numbers generated in software are perhaps better described as ‘pseudo-random’ because the source of randomness may simply be the system clock. The degree of randomness, or entropy, of a system is one the primary factors that determine how difficult it is to hack. The more random the number generator, the more secure the system [6].
A hardware security module (HSM) can be used to generate more secure keys to be injected into devices on the production floor or remotely. However, this process is extremely expensive – the relevant clean rooms cost millions each year to run – and comes with risks. It involves multiple third parties in the supply chain, multiplying the risk of malicious theft or unintentional leakage of the keys.
Fortunately, there is a more secure alternative which gives end users complete control of IoT security, from chip-to-cloud. It starts with building the seeds of the RoT into the silicon itself, exploiting ‘physical unclonable functions’.
The role of physical unclonable functions, or PUFs, in hardware security
Each semiconductor chip is unique by virtue of tiny differences created in its silicon die during the manufacturing process. Such differences can be used to create physical (or physically) unclonable functions, or PUFs, which can contribute to robust security.
PUFs are used to identify silicon chips in a similar way that fingerprints, or iris recognition, are used to identify people. If you can use hardware IP to generate the identities and keys it is far more secure than the common practice of injecting these, and significantly less expensive. However, not all methods of creating such a fingerprint are equally secure or equally cost-effective.
Identities and cryptographic keys are generated on demand to eliminate the need for storage
Crypto Quantique’s hardware IP – QDID™ – enables multiple identities and their related cryptographic keys to be generated in silicon on demand. No secure key storage is needed, enabling on-chip memory to be reserved for other functions and making IoT systems less susceptible to side-channel attacks.
Such attacks try to extract data from devices by accessing, measuring, and analyzing physical parameters like timing, current consumption, and electromagnetic emissions. If you don’t need to store the keys, this risk is minimized.

Part 4
Are all PUFs equally secure?
For an IoT system to be secure today and in the post-quantum era, its RoT must be based upon quantum-driven entropy, or randomness. What does this mean?
PUFs can be categorized by how the variations in silicon chips are measured or by how the randomness is derived. First-generation PUFs were derived by measuring physical characteristics. They are less secure than second-generation PUFs, which are derived from measuring quantum effects.
The quantum computing era will demand quantum-driven security for IoT systems. And even if that era has not yet arrived, quantum-driven security gives better protection for today’s systems too.
It is also worth noting that first-generation PUFs typically generate only a single seed for random number generation, and often still rely on key injection for cryptographic additional keys – such keys residing in packable memory. Fundamentally, these devices don’t solve the security or cost issues at the heart of IoT.
QDID exploits randomness in the thickness of an oxide layer on silicon wafers resulting from manufacturing variability. The extent of quantum tunnelling – a phenomenon whereby electrons propagate through barriers in the fabric of the wafers – varies with the thickness of the oxide layer [7]. QDID measures these quantum effects to generate multiple, uncorrelated cryptographic keys inside the silicon chips made from the wafers. The keys can be used for identities, cryptography, and authentication.
This unique approach eliminates the need for keys to be injected or stored, simultaneously reducing system costs while increasing security. Crucially, having multiple, uncorrelated keys also results in the microcontroller (or other device containing the QDID) to be usable for multiple purposes, and even to be passed to a new owner, allowing secure use of the IoT device.
Part 5
Now you have a secure root-of-trust, what next?
So, you have an IoT endpoint device with an integral, secure identity and the ability to produce multiple, secure cryptographic keys on demand.
How do you connect it to your application without compromising that security?
The major cloud providers all offer some elements of what you need if you’re familiar with using APIs or are happy to spend a lot of time writing your own. But there is a void between hardware, embedded systems and cloud computing that you need to bridge, and it can become a complex and frustrating process. In industrial applications, engineers are skilled in the systems and protocols that have come to dominate the industry in recent years. PLCs, Modbus, RS432, and Ethernet are familiar terminology.

Cryptography is like a new language and one that’s not easy to learn. That’s why security has been one of the factors holding back the wider IoT adoption in these applications and others.
What’s needed is a universal platform, hosted on a server, that connects IoT devices to the cloud, or several clouds, quickly and easily. And it needs to be a platform that does not demand cryptographic expertise to use it. After all, think how many fewer car drivers there would be if they had to be qualified mechanics to get behind the wheel.
QuarkLink™ is one platform that addresses this challenge, without compromising security, without you having to depend on third-party support, and without you having to connect devices one at a time. It will work with RoTs from Crypto Quantique’s partners and, most securely, with devices that employ Crypto Quantique’s QDID, quantum-driven RoT hardware IP.

Part 6
The three fundamental roles of an end-to-end IoT security platform
An end-to-end IoT security platform has to perform three main roles:
-
Provisioning the IoT devices.
-
Onboarding those devices to a server so that they can access applications.
-
Managing the devices throughout their lifecycle.
Here’s how QuarkLink tackles these tasks to deliver seamless cloud connectivity.
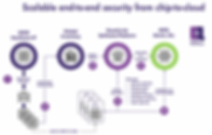
1. Provisioning IoT devices
Provisioning means configuring IoT devices so that they can do something with the data that they collect – the temperature readings from sensors, for example.
The first thing that needs to be done when deploying Crypto Quantique’s technology, is to inject a firmware image into the semiconductor device at the initial programming stage. The QuarkLink platform then manages the remainder of the process. This is what you do with it:
-
Check if an identity has been established for each device.
-
If not, ask the cryptographic engines inside the devices to generate pairs of asymmetric keys – the enrolment keys – from which their identities can be extracted. It’s important to note that neither the identities nor cryptographic keys leave the devices. As mentioned earlier, the keys have been generated by the silicon itself.
-
Create a batch – say, 1,000 fridges – in the QuarkLink console and choose the server policy to associate the batch with a specific cloud account and its privileges.
-
Import the identities of the fridges to QuarkLink.
-
The devices generate certificate sign-on requests (CSRs) and send them to QuarkLink.
-
Upon receiving them, QuarkLink confirms the device identities before returning the certificates.
2. Onboarding IoT devices
So far, the server doesn’t know anything about the endpoint devices. They haven’t been onboarded.
-
QuarkLink sends verification certificates and credentials to the server to tell it that if the devices try to communicate with it, they may be onboarded.
-
The connections are established, and the sensor data from the devices are sent to the server.
The QuarkLink console shows the status of the connection and details of the security certificates for each device. It also allows the user to check that the data has been correctly received at the server.
This secure connection has been achieved in seconds with just a few keystrokes. And in larger deployments, QuarkLink can onboard thousands of devices to one or more servers simultaneously.
Perhaps most importantly, QuarkLink gives full control to the user in preserving security and privacy. And while it currently supports AWS, Microsoft Azure, and Mosquito cloud servers, QuarkLink is infrastructure-agnostic and can be adapted to run on any server– including those within private networks. What’s more, it can secure any microcontroller or ASIC if either QDID or an alternative RoT is available.
3. IoT device management
The management of IoT devices has five main facets:
-
Monitoring their functional integrity and ensuring that they have not been compromised by a cyberattack.
-
Firmware signing and encryption to enable and secure updates over the air (OTA).
-
Key and certificate renewal, which may be needed after the system has a fault or needs reconfiguration.
-
Device revocation if it is compromised and must be disconnected from the server.
-
Subsequent re-onboarding if the device is being passed to a new owner.
QuarkLink enables system owners and operators to manage all of these functions via a simple graphical user interface based on drop-down menus and action buttons.
Part 7
How IoT security must encompass both hardware and software to be effective
The IoT security market is now awash with software vendors promising secure solutions.
But however smart the tools appear to be, the fundamentals of cybersecurity do not change.

Here are the most important questions you need to ask, and why.
-
Are device identities created in hardware or software?
If the answer is software, there is always the risk that someone else’s software may compromise security.
-
If the identities are created in hardware, how are these and the associated cryptographic keys generated?
If this is done by measuring physical parameters, there may be a good degree of entropy, but the outcome is still deterministic. Such a solution may provide a reasonable level of security today, but its efficacy may well be compromised in the post-quantum computing environment that is just around the corner.
-
How comprehensive and well-integrated are the hardware and software elements of the solution?
To maximize security, you need to minimize the involvement of third parties by selecting a fully integrated, chip-to-cloud security architecture.
Q:Architecture, which comprises the QDID quantum-driven hardware IP block and QuarkLink universal IoT security platform, was designed from the ground up to meet not only today’s IoT security challenges but also those that will arrive in the wake of quantum computing. Scalable IoT security has never before been so powerful, and yet so easy to implement.
Q:Architecture has closed the IoT security gap.
Watch this 10 minute demonstration to see the QuarkLink universal security management platform in action with Renesas RA Series microcontrollers.
If you want to take end-to-end control of scalable IoT security, please contact us to discuss how we can help.
[1] https://iot-analytics.com/iot-market-forecasts-overview/
[2] https://crsreports.congress.gov/product/pdf/IF/IF11239
[3] https://www.iot-now.com/2020/01/16/100722-missing-41bn-iot-devices-biggest-prediction-miss-history/
[5] https://mobilenewscwp.co.uk/Unified-Comms/article/number-cyber-attacks-uk-businesses-surge-2020
[6] https://simple.wikipedia.org/wiki/Entropy
[7] https://www.chemistryworld.com/news/explainer-what-is-quantum-tunnelling/4012210.article